Vault Liquidity Frameworks
Strategy Execution
Understanding VLF strategy execution and merkle verification system
VLF-allocated assets must interact with integrated protocols through actual VLF strategies. This strategy execution process is performed by the Strategist and is only possible within the rules registered on-chain, ensuring assets cannot be used in unintended ways or misappropriated.
 The strategy execution system provides a secure, flexible framework for DeFi integrations while maintaining strict asset protection through cryptographic verification.
Parameter Requirements:
Sanitization Benefits:
The
The strategy execution system provides a secure, flexible framework for DeFi integrations while maintaining strict asset protection through cryptographic verification.
Parameter Requirements:
Sanitization Benefits:
The
 The strategy execution system provides a secure, flexible framework for DeFi integrations while maintaining strict asset protection through cryptographic verification.
The strategy execution system provides a secure, flexible framework for DeFi integrations while maintaining strict asset protection through cryptographic verification.
Strategy Execution Process
Step 1: Strategy Preparation & Input Validation
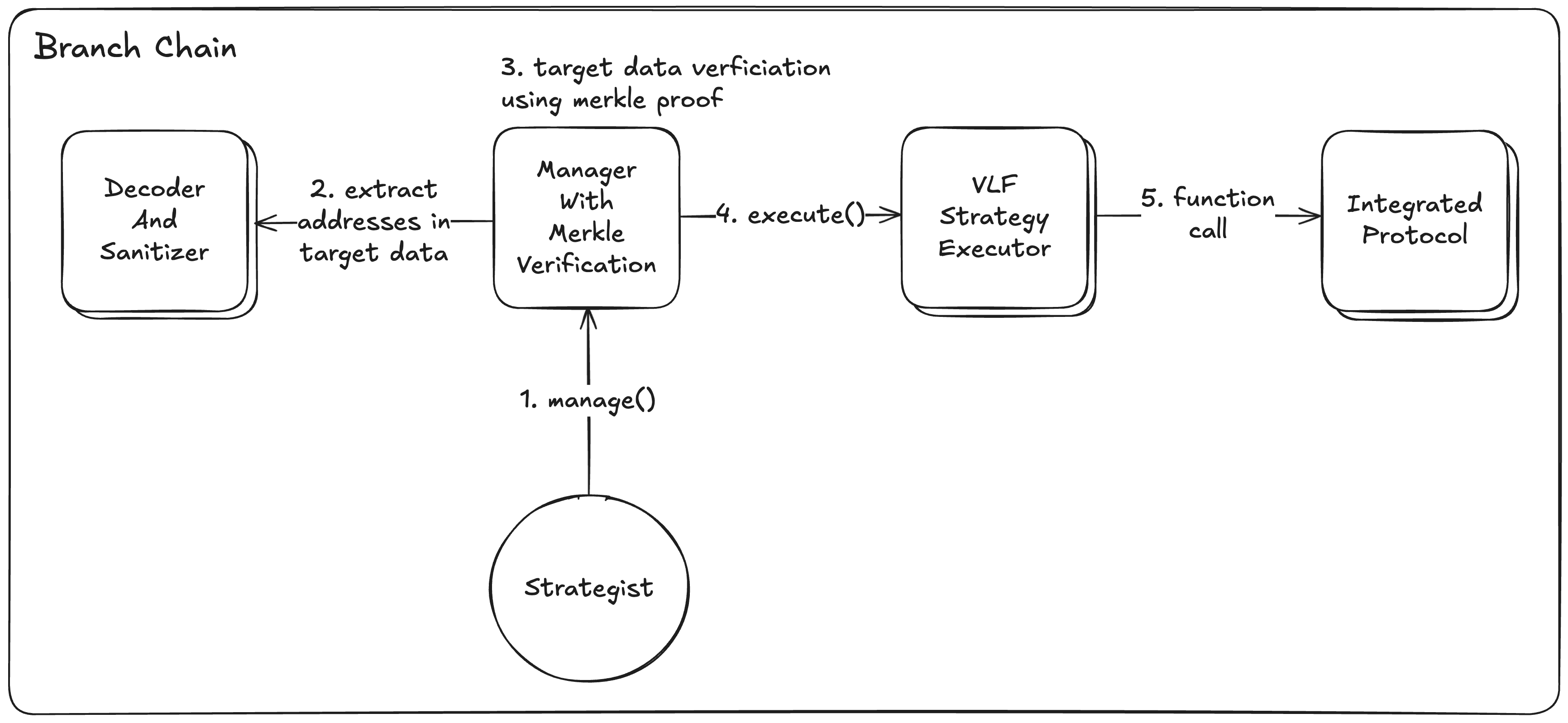
Before execution begins, the strategist prepares the strategy execution by gathering all required components. The core security mechanism relies on merkle tree verification to ensure only approved strategies can be executed. The strategist interacts with VLF Strategy Executors through the ManagerWithMerkleVerification contract’smanage() function, which requires the following parameters:
- strategyExecutor: The VLF Strategy Executor contract that will execute the strategies
- manageProofs: Merkle proofs verifying each function call is pre-approved
- decodersAndSanitizers: Contracts that decode and sanitize function call parameters
- targets: Target contract addresses for the DeFi protocol interactions
- targetData: Encoded function call data for each target
- values: MITO amounts to transfer with each function call
Step 2: Merkle Proof Verification
During the execution process, the system performs cryptographic merkle proof verification to confirm that each function call is pre-approved. This process includes parameter sanitization and authorization validation to ensure secure strategy execution. The Verification Process:- Parameter Sanitization: The
decoderAndSanitizercontract extracts only security-relevant parameters from function call data, filtering out parameters that don’t affect authorization - Merkle Proof Verification: The sanitized data is then verified against the merkle tree to confirm the function call is pre-approved
decoderAndSanitizer approach provides crucial system advantages:
- Selective Parameter Verification: Only security-critical addresses are included in verification, while non-critical parameters are filtered out
- Reduced Merkle Tree Complexity: By ignoring non-security parameters, the number of required merkle tree leaves is dramatically reduced
- Enhanced Flexibility: Strategists can adjust trading parameters without requiring new merkle tree updates

